Wordfence analysts report having detected a massive wave of attacks in the last couple of days, originating from 16,000 IPs and targeting over 1.6 million WordPress sites.
The threat actors target four WordPress plugins and fifteen Epsilon Framework themes, one of which has no available patch.
Some of the targeted plugins were patched all the way back in 2018, while others had their vulnerabilities addressed as recently as this week.
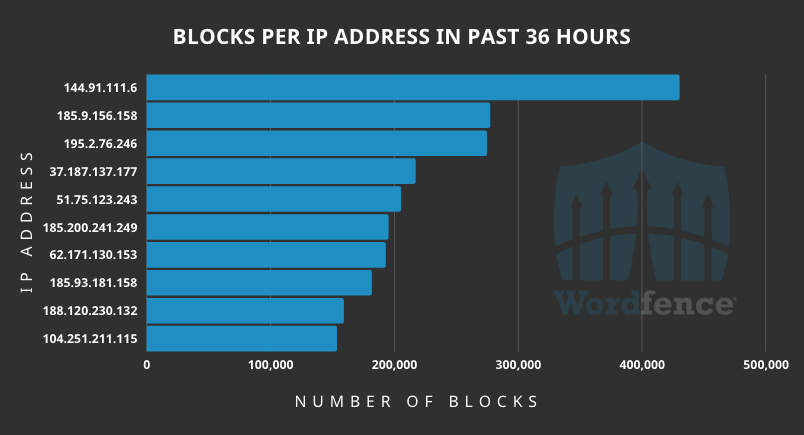
IP addresses launching the attacks
Source: Wordfence
The affected plugins and their versions are:
- PublishPress Capabilities
- Kiwi Social Plugin
- Pinterest Automatic
- WordPress Automatic
The targeted Epsilon Framework themes are:
- Shapely
- NewsMag
- Activello
- Illdy
- Allegiant
- Newspaper X
- Pixova Lite
- Brilliance
- MedZone Lite
- Regina Lite
- Transcend
- Affluent
- Bonkers
- Antreas
- NatureMag Lite – No patch available
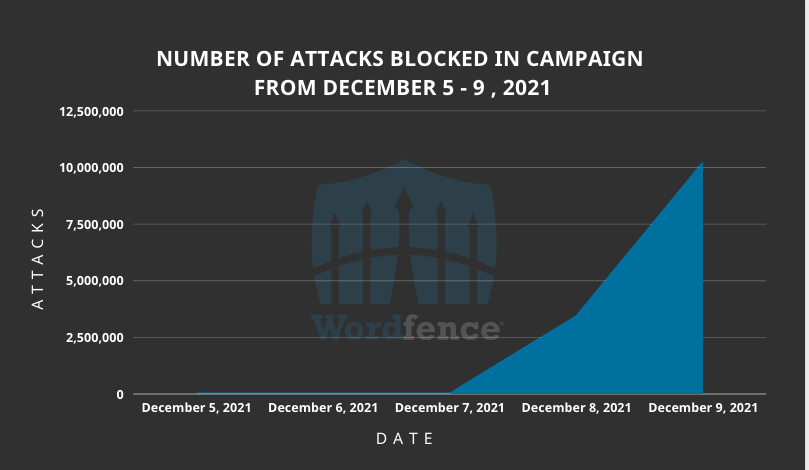
Source: Wordfence
“In most cases, the attackers are updating the users_can_register option to enabled and setting the default_role option to administrator,” Wordfence explains.
“This makes it possible for attackers to register on any site as an administrator effectively taking over the site.”
Also Read: HACKERS DEPLOY LINUX MALWARE, WEB SKIMMER ON E-COMMERCE SERVERS
Check, update, clean WordPress sites
To check if your site has already been compromised, you can review all user accounts and look for any rogue additions that should be removed immediately.
Next, review the site’s settings at “http://examplesite[.]com/wp-admin/options-general.php” and pay attention to the Membership and the new user default role setting.
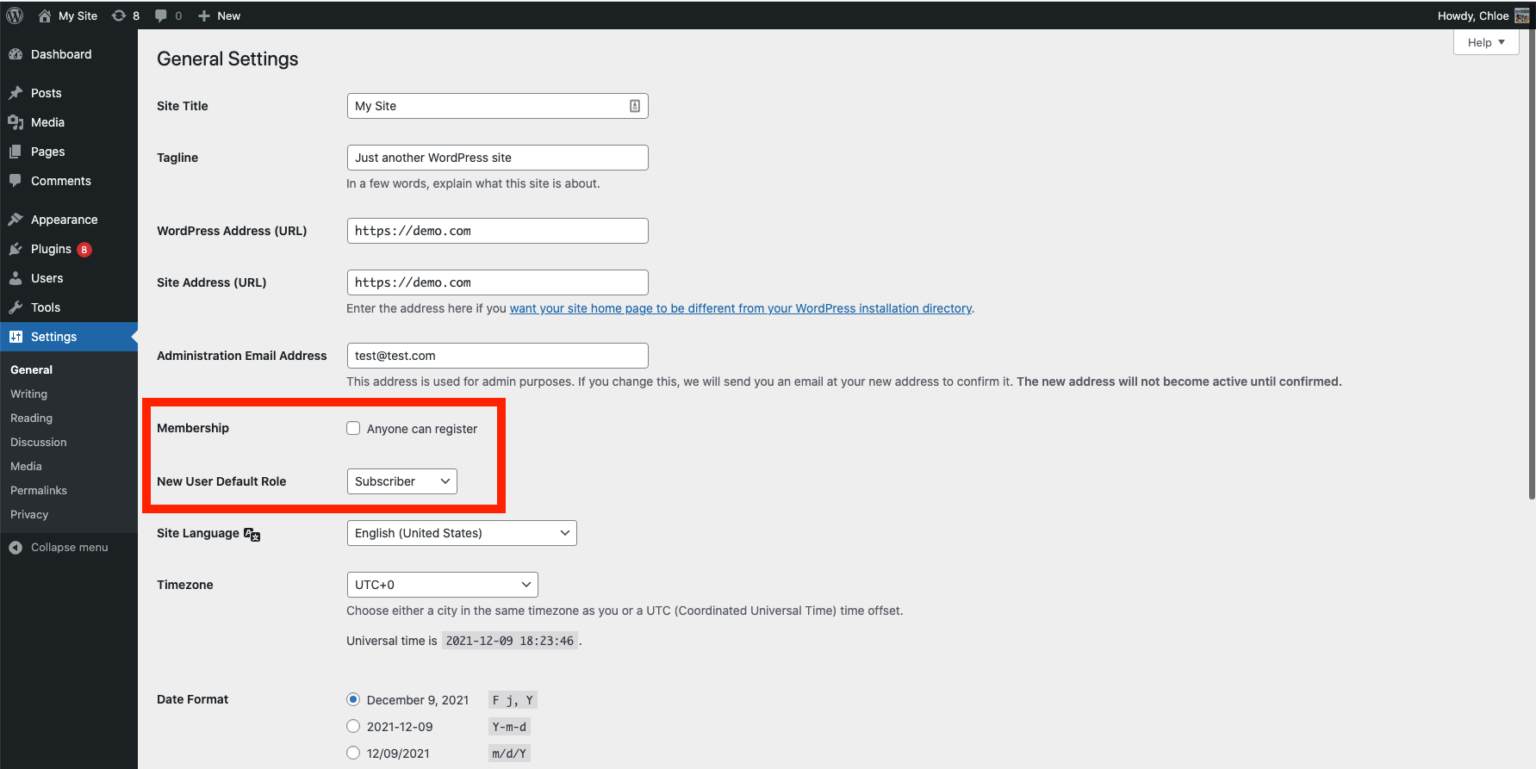
Source: Wordfence
It is recommended to update your plugins and themes as soon as possible, even if they’re not in the above list. If you’re using NatureMag Lite, for which there’s no fix, you should uninstall it immediately.
Note that updating the plugins won’t eliminate the threat if your site has already been compromised. In this case, you are advised to follow the instructions found in detailed clean-up guides first.
In general, try to keep the number of plugins at your WordPress site to the absolute minimum necessary as this dramatically reduces the chances of being targeted and hacked in the first place.
Credits: bleepingcomputer.com


